- Secure SDLC Governance
- Threat Modeling & Risk Assessment
- Secure Architecture Standards
DevSecOps Compliance Automation for Financial Institutions — Without Slowing Delivery
Through structured alignment across all three lines of defense, ISATech.ai transforms DevSecOps from a technical practice into a board-governed control domain.
Book a Consultation
Know Your Risks Before They Know You.

Compliance Built Into the Code — Not Bolted On.

Audit-Ready by Design. Always.
Who We Are
ISATech Advisory is a DevSecOps consulting firm dedicated to helping financial institutions build and deliver software safely and compliantly.
We partner with banks and financial institutions to embed regulatory controls into your delivery pipelines, align tooling and platforms with audit expectations, and provide continuous visibility into control effectiveness—so you can ship with confidence.
Why partner with us
- Compliance by design—controls embedded in delivery
- Audit-ready evidence generated automatically
- Framework that scales from PLAN through GOVERN
CI/CD pipeline → audit report (ISATech 16 Core Secure Delivery Controls × all control IDs)
We evaluate using ISATech 16 Core Secure Delivery Controls. Each checkpoint is a compliance seal—you’ve got the seal. Pipeline output: one audit report per run.
First advisory stage output
- A 5-Level DevSecOps Maturity Model (used in discovery to assess gaps in compliance, governance, pipeline & auditability)
- Integrated regulatory crosswalk mapping
- Audit-ready evidence definitions
5-Level DevSecOps Maturity Model
Part of our initial discovery engagement: we use this model to assess your gaps in compliance, governance, pipeline, and auditability. The same model can be used to reassess progress as you implement phases from PLAN through GOVERN and as new regulations and control requirements are enacted. Each control is scored 1–5 (red → green) for quantitative scoring and board reporting.
- Level 1
- Ad Hoc
- Level 2
- Basic
- Level 3
- Defined
- Level 4
- Managed
- Level 5
- Optimized (Policy-as-Code / Continuous Compliance)
What Sets Us Apart
- Aligns DevSecOps execution to risk oversight
- Embeds regulatory defensibility into technical controls
- Enables audit readiness by design
- Reduces governance translation friction
- Provides measurable maturity progression
Through structured alignment across all three lines of defense, ISATech.ai transforms DevSecOps from a technical practice into a board-governed control domain.
Services
We deliver the full PLAN → GOVERN framework, or hand off the implementation roadmap to your in-house DevOps team. Our framework consists of six phases, from PLAN through GOVERN.
- Source Code Access Governance
- CI/CD Pipeline Security Controls
- Secrets Management in Pipelines
- Static & Dynamic Security Testing (SAST/DAST)
- Software Composition Analysis (SCA)
- Secure Code Review Governance
- Deployment Approval & Change Traceability
- Environment Segregation & Promotion Controls
- Secure Configuration Baselines
- Vulnerability Management & Patch Governance
- Logging & Monitoring Controls
- Exception Management & Risk Acceptance
- DevSecOps Maturity Measurement & Reporting
Flexible Engagement Model — We deliver the full PLAN → GOVERN framework, or hand off the implementation roadmap to your in-house DevOps team and continue as a strategic compliance advisor as they build. You choose the level of involvement that works for your organization.
How We Work
A clear 3-step process from discovery to audit readiness
Discovery (4–6 Weeks)
We conduct a thorough gap analysis and control mapping review to identify compliance risks before any automation begins.
Automation Build
We design and implement CI/CD pipelines that automatically generate audit-ready compliance evidence mapped to your regulatory framework.
Audit Readiness
Continuous monitoring and reporting keeps you inspection-ready at all times—without disrupting delivery.
About Us
Founder Name
Title
[2–3 sentences on background and experience in DevOps, compliance, or financial services.]
[1 sentence on their contribution to ISATech.ai.]
Founder Name
Title
[2–3 sentences on background and experience.]
[1 sentence on their contribution to ISATech.ai.]
Founder Name
Title
[2–3 sentences on background and experience.]
[1 sentence on their contribution to ISATech.ai.]
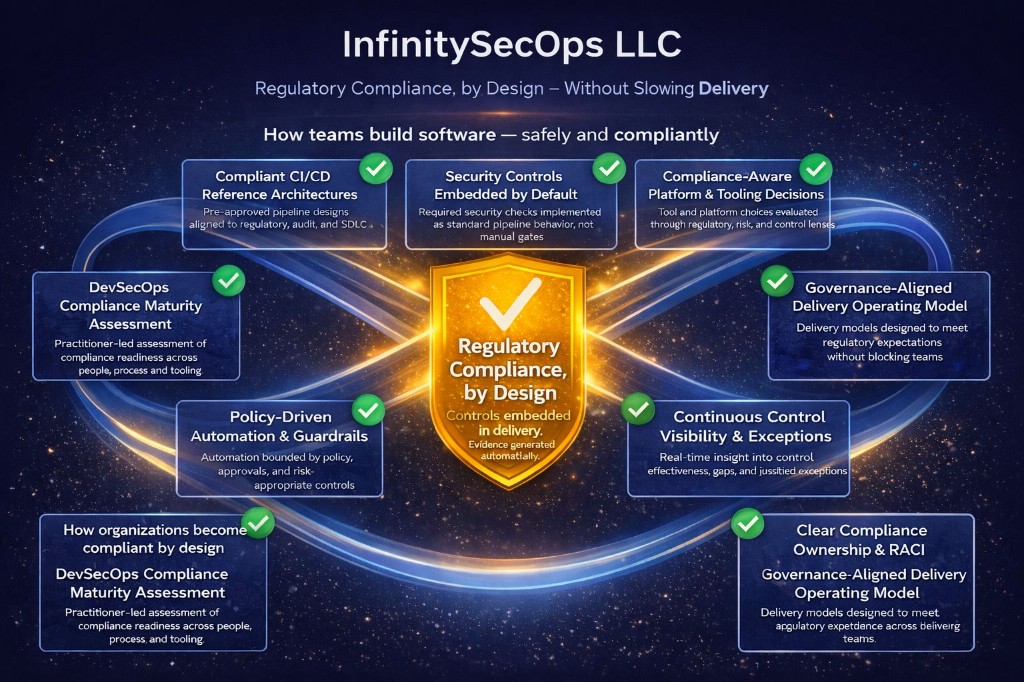
Our methodology: regulatory compliance by design
Contact Us
Ready to build compliantly? Get in touch for a consultation.

